
As we embark on the milestone year of our 25th anniversary, we would like to take a moment to share some of the high points of our past and some exciting developments that lie ahead in 2024 and beyond.
1999-2024: A Journey of Technological Advancement
Over the past decades, CTG has been at the forefront of technological evolution, adapting to the ever-changing landscape of corporate needs. From our humble beginnings in 1999 to navigating the complexities of the digital age that began in the 2010s, our journey has been marked by innovation, dedication, and a relentless commitment to excellence.
2024: Celebrating 25 Years of Excellence
As we reflect on the accomplishments that have shaped CTG into the industry leader it is today. Our success has been a testament to the unwavering dedication of our team and the enduring partnerships we have forged with businesses across Hudson, Ohio, and beyond.
Our commitment to helping businesses thrive in an era that not only demands a higher level of productivity and technology from its users and technical environment, but with the expectation of limited mitigated risk to the end client. As we must also recognize the diverse needs of our clients; we are introducing a range of new offerings aimed at providing innovative and integrated solutions.
In addition to our business phone and internet solutions, this innovation is evident in our enhanced cloud services, where we build upon our established expertise in cloud computing to provide businesses with advanced solutions that ensure both seamless scalability and uncompromising security. Additionally, CTG is venturing into introducing solutions that connect businesses to the future – such as Internet of Things, energy, and mobility. In true CTG fashion, we are also expanding our suite of managed services and cyber security solutions to help alleviate the complexities of technology management, allowing businesses to focus on their core objectives.
2024 and Beyond: Shaping the Future of “Corporate Technology”
As we stand on the cusp of our 25th year, Corporate Technologies Group is not just celebrating a milestone; we are envisioning the future. Together with our clients, partners, and the community, we look forward to shaping a future where technology is a catalyst for positive change for your business.
Thank you for being a part of our journey, and here is to a continuing partnership of pushing boundaries and redefining excellence in the world of “corporate technology.”
#MoveTechForward

This quarterly publication provided courtesy of Brett Harney, President of CTG.
Strengthen Your Business With A Business Continuity Plan
The season of spring cleaning our homes, scheduled auto repairs, and checking our storm windows is fast approaching. This is also the season of severe storms, power outages, and expected sick days. In the unpredictable world of business, every moment counts, with downtime costing SMBs between $137 to $427 per minute, as per a 2020 IBM report.

This month, amidst the chaos, let's not forget to prepare our business with our Business Continuity Plan (BCP).
-
A BCP, short for Business Continuity Plan, is your blueprint to keep your business running seamlessly in the face of unplanned events, whether it's a natural disaster, a cyber-attack, or human error. It goes beyond just restoring IT systems, encompassing operations, assets, human resources, technology, and safety to ensure vital functions are maintained until the crisis is resolved.
Some might confuse it with a disaster recovery plan, which focuses solely on restoring IT systems. However, a BCP is a comprehensive framework for your entire company's resiliency and financial sustainability.
Why is a BCP essential? Imagine a major fire incident at your office. Do you know where and how your employees would work? Could they handle customer calls? Where would your executive team meet for critical decisions? A BCP not only provides a plan for restoring IT systems but also offers a practical framework for your company's overall resiliency and financial sustainability.
So, what does your BCP need?
- Identify your company's critical functions.
- Conduct a risk assessment.
- Develop recovery strategies for each critical function.
- Ensure data backup and recovery are in place.
- Establish a communication plan.
- Plan for alternative operations.
- Schedule regular reviews and updates.
Every business, big or small, is at risk of a disaster. According to a 2022 threat report by ConnectWise, nearly two in three midsize businesses experienced a ransomware attack in the last 18 months. The goal of a BCP is to minimize disruption and facilitate a swift return to normal operations.
Take this opportunity to review your BCP with your team. If you don't have one, consider this your sign to get it done.
Stay resilient, Brett Harney Owner, Corporate Technologies Group
Free Report Download: The Business Owner’s Guide To IT Support Services and Fees
Learn about:
- Common ways IT companies charge for services.
- Billing models and potential risks.
- Exclusions and hidden fees in IT contracts.
- Avoiding unexpected costs.
Claim your FREE copy today at
https://ctgusa.net/wp-content/uploads/2024/02/itbuyersguide.pdf
DID YOU KNOW…
Downtime costing SMBs between $137 to $427 per minute
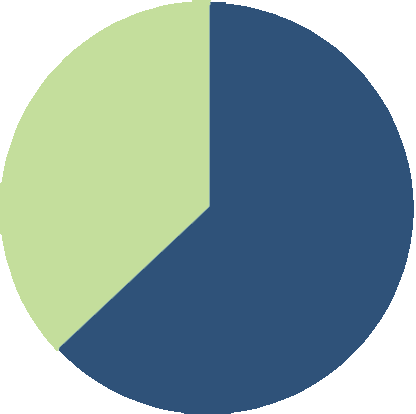
Nearly two in three midsize businesses experienced a ransomware attack in the last 18 months
Old Malware, New Tricks
Choosing the Right Password Manager
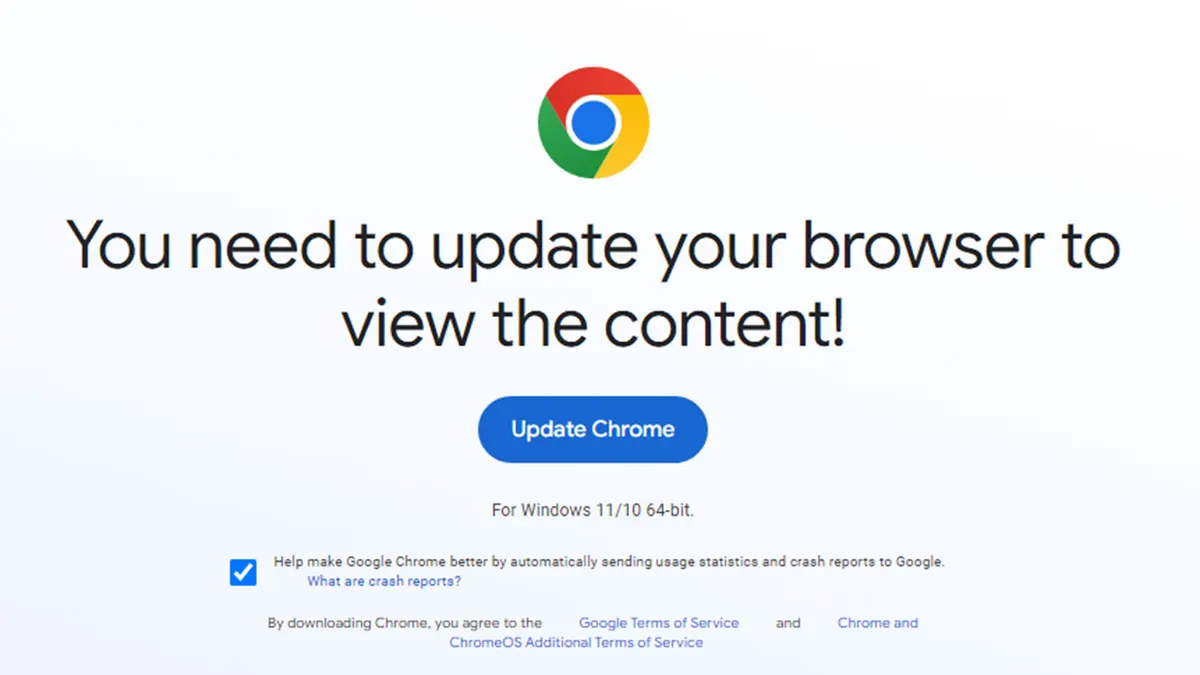
Hackers compromise a website, replacing content with a deceptive browser update prompt. Clicking on the update button downloads malware. New tactics involve storing files on cloud services or cryptocurrency blockchains, making removal challenging.
A cybersecurity expert, Randy McEoin, uncovered a scam known as ClearFake in August 2023. This malicious scheme targets users through compromised WordPress sites, displaying fake messages urging them to update their browsers. The precision is noteworthy, tailoring alerts to specific browsers such as Chrome, complete with a tempting blue update button. Unfortunately, clicking on this deceptive update prompts the download of malicious software designed to compromise user information.
Exploiting users' trust in familiar sites, these scams manipulate end user’s familiarity with known sources. This scam aims to trick users into downloading malware that can compromise devices and expose personal information.
To safeguard against such threats, ensure your team is trained to only rely on official sources for updates. Prioritizing strong antivirus protection can help your business to defend against evolving cyber threats. Investing in robust antivirus protection across all devices and maintaining up-to-date operating software is crucial.
The proactive approach involves having antivirus software actively running to alert users of potential threats, caution against clicking on suspicious links, and ultimately protect against hacking attempts. Penetration Testing (or pen testing) is another effective security measure you can take to secure your network.
Protect Yourself
No legitimate browser update will ever prompt a pop-up. Check your browser status through settings. Use effective antivirus protection and train your team to recognize this evolving scam. Click this link to read more about the ClearFake scam: https://nypost.com/2023/11/28/tech/apple-users-warned-that-fake-chrome-update-steals-money-passwords/
Protect Yourself
The amount of time it takes to detect a hacking incident is longer than you may realize. In fact, the average business can take up to 197 days to recognize a data breach. While individuals may spot hacking more swiftly on personal accounts, in a work environment, it’s not guaranteed to find it fast enough to avoid damage. However, there are some telltale signs that you can look for to help and here are the top 5 signs that your network has possibly been hacked.

DID YOU KNOW...
The average business can take up to 197 days to recognize a data breach.
Unusual Network Activity:
- Explanation: Keep an eye on your network traffic, which is like the digital flow of information between devices. If you notice a sudden increase in data transfer or strange patterns, it could be a sign of unauthorized access.
- Example: Imagine your network as a highway. If suddenly there's a massive traffic jam where it shouldn't be, that's a red flag.
- Solution: This can be semi-solved with data flow monitoring, DLP mechanisms, data classification, alerting profiles, etc.
Unexpected System Behavior:
- Explanation: If your computer or server starts acting strangely – crashing, slowing down, or freezing without an apparent reason – it could indicate a breach.
- Example: It's like your car suddenly making weird noises or stalling when it usually runs smoothly. Something might be wrong under the hood.
- Solution: Checking task manager immediately, run virus scans, use other tools that can be downloaded for free such as rkill and tron.
Unknown Accounts or Devices:
- Explanation: Regularly check for unfamiliar user accounts or devices connected to your network. Hackers often create their own accounts for future access.
- Example: Think of your network as a party. If you see someone you don't recognize, they might not be on the guest list.
- Solution: Alert profiles through an RMM can let you know when this happens, SIEM/SOC solutions can detect this behavior.
Unexplained Data or File Changes:
- Explanation: Keep an eye on your important files and data. If you notice unexpected changes, deletions, or new files, it could be a sign of unauthorized access.
- Example: Imagine your important documents as a bookshelf. If books are missing or new ones appear without your knowledge, something's not right.
- Solution: File Integrity solutions can help with this. Data classification software can track this.
Security Warnings or Alerts:
- Explanation: Pay attention to security software alerts or warnings. If you receive messages about potential threats or breaches, take them seriously.
- Example: It's like your security system at home alerting you when someone tries to break in. You wouldn't ignore it.
- Solution: Investigation is the most important here. Learning what to look for.
Being as that CTG itself must meet the PCI DSS compliance, we have firsthand knowledge and experience with the hurdles. Our in-house services, such as our managed services offering, and assessment offering can help businesses meet the requirements of their compliance and do so honestly and completely. CTG also offers continual support in compliance management as well as can provide most if not all the needed platforms and services to meet, not only PCI but most other compliances. Any area that is outside of the scope of internal CTG services can be provided by our thoroughly vetted and reputable partner community. Below are some references that I encourage anyone reading this, or anyone that must deal with PCI compliance to check out to get a better understanding of what you need to accomplish to meet this standard. And of course, please reach out to CTG to have a deeper conversation about the places we are helping.


